Delegatecall to Untrusted Contracts: A Dangerous Backdoor in Ethereum Smart Contracts

The delegatecall function is a powerful but risky feature in Solidity smart contracts. While it can enable modular and upgradable contract designs, improper use,especially with untrusted addresses—can lead to catastrophic vulnerabilities.
Let’s break down what delegatecall does, why it’s risky, and how to use it safely.
What Is Delegatecall in Solidity?
In Solidity, delegatecall is a low-level function that allows one contract to execute the code of another contract in its own context. That means:
-
The code runs from the callee (target) contract.
-
But the storage,
msg.sender, andmsg.valuecome from the caller contract.
Essentially, it’s like giving another contract temporary access to run logic as if it were part of your own contract,with full access to your state variables.
This can be useful in cases like proxy patterns or contract upgrades, where the logic lives separately from the data. But it also opens the door to serious risks.
Vulnerabilities Caused by Delegatecall to Untrusted Callee
1. State Variable Collisions
This is the most common and dangerous issue. Since delegatecall runs code in the context of your contract, it can overwrite your contract’s storage variables.
If the callee contract’s storage layout doesn’t perfectly match the caller’s layout, values like owner, balances, or critical configuration settings could be accidentally or maliciously altered.
✅ Example: If the target contract writes to storage slot 0, but in your contract slot 0 holds your admin address, the admin could be overwritten by a malicious value.
2. Unintended Authority Escalation
Because the logic runs with your contract's privileges, the destination contract may unintentionally gain access to high-privilege operations like:
-
Transferring Ether or tokens
-
Changing ownership
-
Modifying access control settings
If that external contract is controlled by an attacker, they can abuse your privileges to drain funds or seize control.
3. Logic Errors and Exploitable Attacks
The flexibility of delegatecall makes it prone to mistakes. If developers aren't extremely careful, it can:
-
Introduce reentrancy vulnerabilities
-
Bypass business logic safeguards
-
Trigger unintended fallbacks or default behaviors
This is particularly dangerous when the delegatecall target is derived from user input.
Real-World Impact of Using Delegatecall Unsafely
When you use delegatecall on an untrusted or user-controlled address, you're effectively granting that contract full access to your internal state and funds. It’s equivalent to handing your wallet over to someone else and asking them to press buttons on your behalf,with zero oversight.
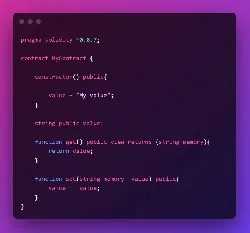
A common attack vector is when a contract uses call or delegatecall with arguments like:
solidity
(bool success, ) = _target.delegatecall(_data);
If _target comes from user input and isn’t validated, an attacker can redirect execution to a malicious contract and gain control over sensitive functions.
Best Practices and How to Protect Your Contracts
To avoid these high-impact risks, developers should follow strict guidelines when using delegatecall:
✅ Avoid User-Defined Targets
Never allow users to specify the target address for delegatecall. This includes passing it as a function argument, setting it via external functions, or pulling it from untrusted sources.
✅ Use a Whitelist
If your design requires dynamic contract references, maintain a strict whitelist of trusted and audited contracts. Validate all target addresses against this list before executing any delegatecall.
✅ Match Storage Layouts
When using delegatecall in proxy patterns (like UUPS or EIP-1967), ensure that the storage layout of the logic contract matches the data layout of the proxy contract exactly.
✅ Use Trusted Libraries
When building upgradable contracts, consider using vetted implementations like OpenZeppelin’s Proxy Contracts. These contracts are designed to safely manage delegatecall and minimize misuse.
With AuditLensPlus, you can uncover vulnerabilities in your smart contracts quickly and cost-effectively, empowering you to take the right steps toward more secure and robust code.
Final Thoughts
delegatecall is a double-edged sword. It empowers smart contract modularity and upgradability but can also introduce high-risk vulnerabilities if misused. Always remember:
“With great power comes great responsibility.”
Treat delegatecall like a nuclear option: only use it when absolutely necessary, and never with untrusted input.